Identify and Respond to Email
Threats Faster with

Contain Data Breaches in Minutes Instead of Months
Identify and respond to email threats faster with PhishER
With automatic prioritization for emails, PhishER™ helps your InfoSec and Security Operations team cut through the inbox noise and respond to the most dangerous threats more quickly.
Because phishing remains the most widely used cyber attack vector, most end users report a lot of email messages they “think” could be potentially malicious to your incident response team.
Whether or not you step employees through security awareness training doesn’t change the fact that your users are likely already reporting potentially dangerous emails in some fashion within your organization. The increase of this email traffic… can present a new problem!
With the firehose of spam and malicious email that attack your network, some 7-10% of these make it past your filters. With only approximately 1 in 10 user-reported emails being verified as actually malicious, how do you not only handle the high-risk phishing attacks and threats, but also effectively manage the other 90% of user-reported messages accurately and efficiently? Now, there is PhishER.
What is PhishER?
PhishER is the key ingredient of an essential security workstream. It’s your lightweight Security Orchestration, Automation and Response (SOAR) platform to orchestrate your threat response and manage the high volume of potentially malicious email messages reported by your users. And, with automatic prioritization of emails, PhishER helps your InfoSec and Security Operations team cut through the inbox noise and respond to the most dangerous threats more quickly.
Additionally, with PhishER you are able to automate the workstream of the 90% of reported emails that are not threats. Incident Response (IR) orchestration can easily deliver immediate efficiencies to your security team, but the potential value is much greater than that.
With the right strategy and planning, your organization can build a fully orchestrated and intelligent SOC that can contend with today’s threats. PhishER enables a critical workstream to help your IR teams work together to mitigate the phishing threat and is suited for any organization that wants to automatically prioritize and manage potentially malicious messages – accurately and fast! PhishER is available as a stand-alone product or as an add-on option for current KnowBe4 customers.
Why Choose PhishER?
PhishER is a simple and easy-to-use web-based platform with critical workstream functionality that serves as your phishing emergency room to identify and respond to user-reported messages. PhishER helps you prioritize and analyze what messages are legitimate and what messages are not – quickly. With PhishER, your team can prioritize, analyze, and manage a large volume of email messages – fast! The goal is to help you and your team prioritize as many messages as possible automatically, with an opportunity to review PhishER’s recommended focus points and take the actions you desire.
With PhishER Security Roles, you can easily distribute your team’s workload of email analysis and dispositioning from within PhishER. Use Limited and Full access Security Roles to implement a multi-tiered incident response system based on the severity levels of your user-reported messages in PhishER.
How PhishER Works
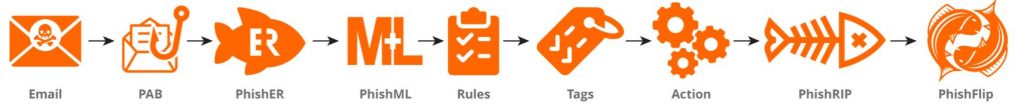
PhishER processes user-reported phishing and other suspicious emails by grouping and categorizing emails based on rules, tags, and actions. PhishML, the custom machine-learning module, analyzes messages and generates confidence values which are used to tag messages. PhishRIP helps you easily find and quarantine suspicious messages still sitting in mailboxes across your entire organization. PhishFlip automatically turns defanged phishing emails into training opportunities by flipping them into simulated phishing campaigns.
Try KnowBe4 Today!
KnowBe4’s Enterprise Awareness Training Programs provides
you with a comprehensive new-school approach that integrates
baseline testing using mock attacks, engaging interactive web-based
training, and continuous assessment through simulated phishing attacks
to build a more resilient and secure organization.








