What’s New in Cyber Threats – Recent Attacks You Should Know About (late 2025)
National Health Data Exposed: What the NHLS Breach Means for South Africa’s Cybersecurity Michael...

Your Data, Always Protected.Private.Safe.Secure.Shielded.With Our Reliable Solutions.
Protecting Your Digital World, One Click at a Time.

At 2TS, we focus on cutting-edge and industry-leading tools to safeguard your information and Operational Technology (IT & OT) Environments against ever-changing cyber threats.

We offer comprehensive, tailored cybersecurity solutions within our technology strategy to meet the unique needs of your industry and protect your critical assets. Allowing you to focus on what matters!

Our team of experts are here to deliver a comprehensive service to ensure that your information stays secure, your compliance requirements are met, and your organisation can operate with confidence.


























A Comprehensive Mobile Device Management (MDM) that provides secure, scalable, and easy-to-manage device and app control for any business.

An integrated Endpoint Management & Security (EPM&S) solution that delivers real-time visibility, security, and automation across IT assets.

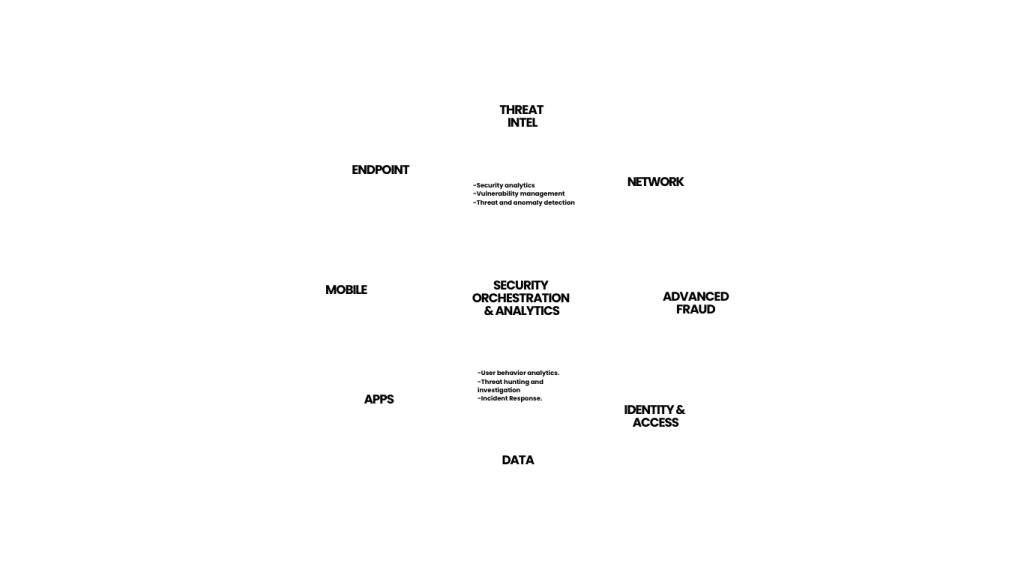
X-Force provides advanced threat intelligence and cybersecurity solutions to help organisations detect, prevent, and respond to cyber threats.

Safeguard your organisations infrastructure by protecting its data, systems, and networks from cyber threats and unauthorised access.

Advanced fraud prevention and malware protection to help organisations secure their digital transactions and safeguard customer data.

Ensure secure and efficient user authentication and authorisation, and access controls across digital systems and resources.

Real-time data activity monitoring and robust security to protect sensitive data and ensure compliance across databases and applications.

An application security testing tool that helps identify and fix vulnerabilities in web and mobile applications to ensure secure development.

A SIEM solution that helps organisations detect, investigate and respond to security threats with real-time data analysis and advanced threat intelligence.
National Health Data Exposed: What the NHLS Breach Means for South Africa’s Cybersecurity Michael...