Our News & Videos
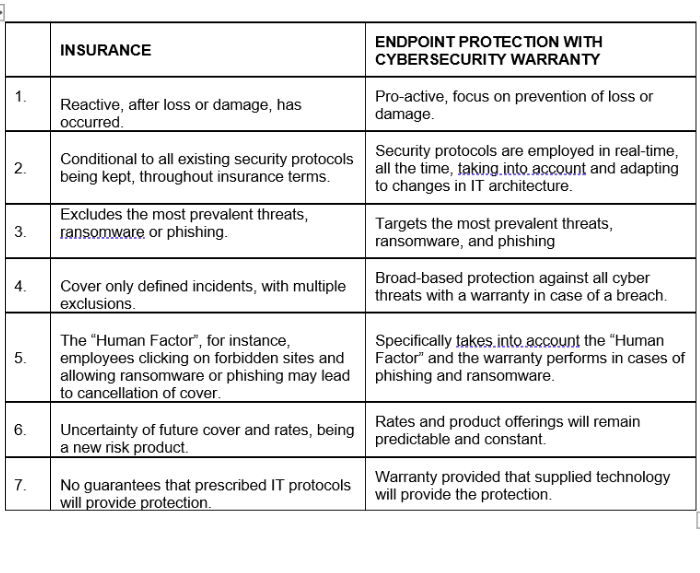
Cyber Insurance vs. Cyber Warranty. How do they differ?

Some of the challenges faced by insurers are:
- Insufficient statistical data to develop robust underwriting models. Qualitative, semi-qualitative, and qualitative data are critical components for the development of rating algorithms and are essential for the development of successful underwriting models. Notwithstanding cyber insurance becoming the fastest growing insurance risk globally, insurers are adopting a cautious pricing approach for fear of “getting burned”.
- Cyber insurance underwriting has also proven to be fiendishly difficult due to constantly evolving technology, making it almost impossible for insurers to model the risk.
- A previously assessed cyber risk can change in a heartbeat.
- Ignorance – the majority of technology users are not “tech-savvy” creating an ideal environment for hackers to practice their trade.
- Insurance incidents need to be “accidental and fortuitous” and not predictable – on a “likelihood matrix” cyber risks can be classified as “almost certain”. This rather favours the application of risk management principles as opposed to transferring the risk to an insurer.
A comparison with, for instance, vehicle insurance will perhaps illustrate the insurance challenge – vehicle insurance provides clear information on the manufacturer, model or series, engine specifications as well as colour, just to mention only a few aspects to uniquely identify the asset.
Likewise, the nature of the insured risk can be priced with relative accuracy. In the event of a vehicle claim, a loss adjuster will perform a standard evaluation. Should it then become evident that, for instance, the vehicle’s engine, the actual model, and colour has changed since the cover was incepted, a claim would simply not be entertained, for obvious reasons.
When underwriting an insurance policy for an industry as fluid as information security, it becomes almost impossible, because, even by the time the cyber insurance policy is issued, the insured “asset” (the data or information) has in all probability already changed. This creates enormous challenges for insurance companies to price the risk in such a way as not to incur significant underwriting losses.
A presentation by KnowBe4 has revealed that the majority of all malicious digital breaches are due to social engineering and phishing followed by breaches as a result of unpatched software.
An effective risk management strategy would therefore be to focus on preventative measures (risk avoidance) in areas where cyber risks originate.
The Top Ransomware Vectors for 2021 in order of prevalence are:
1. Email & Phishing
2. Unpatched software
3. Remote Desktop Protocol & Weak Passwords
4. USB key and other minority causes
The simplicity of the problem may perhaps startle all those organisations grappling with cyber defense – the root cause of the majority of breaches can in most instances be traced to the day-to-day social interactions happening via the oldest channel – emails!
Most IT departments still regard as de rigueur the more “advanced” Key Performance Indicators in cybersecurity, rather than addressing the real threat – effective end-point protection.

Securing the company’s network with the latest “tech” is still viewed as the “ultimate solution” with paltry focus on protecting information and data where it matters most – the entry point! This critical area of responsibility, if attended to at all, is routinely placed in the care of the most junior members of the IT team.
If in the affirmative, the follow-up, equally important question is if such protection is extended, not just to on-company networks, but also to the off-company networks?
Employees are now, more than ever before, accessing company information through unsecured networks and WIFI connections, which utterly compromises the company’s security architecture, regardless of how sophisticated it may be. Endpoint protection starts with organisations educating their employees on cyber awareness – also known as “the people factor”. It is extremely difficult to control what staff decide to click on, but when they are making informed and educated decisions before clicking, it will go a long way to address the problem.
Viewed from the perspective of cyber insurance, specifically taking into account all of the above, it is apparent that not all insurance products are created equal.
All exclusions and policy conditions should therefore be closely scrutinised, as social engineering exclusions would leave clients without remedy for the most prevalent of risks.
The old adage of “prevention is better than cure” rings especially true for modern cyber risks, as cyber insurance critical as it is, only performs after the breach has occurred. At best it offers partial indemnity against damages and legislative penalties. For instance, in cases of ransomware attacks, irreparable harm is done to businesses’ reputations and continuity, leading to elevated failure rates shortly after those infringements.
Given the severity of the above consequences, it, therefore, makes perfect sense to first employ proactive, preventative measures to reduce the probability of cyber breaches.
The strategy is simple and cost-effective – protect the endpoint from phishing and malware attacks with the help of best-of-breed providers that use the newest and most effective technologies. The provider should have such a high conviction of the efficacy of the solution that a Free Cyber Warranty should be included in their product offering.
Summary and Conclusion:
A universal caveat in all cyber insurance policies is the onus on a client to have continuous protective measures in place as failure to do so will invalidate cover. Compliance is however possible with the prior deployment of advanced technology and systems to monitor threats in real-time. The product provider must, furthermore, back up his conviction by offering a FREE Cyber Warranty in case of a breach, regardless of whether such breach happened when connected to the corporate network or not.
Providers like Thuthukani Technology Solutions will provide protection wherever the client is, on or off the corporate network. Thuthukani Technology Solutions includes FREE Cyber Warranties with their solutions and provides assurance that clients have a quality cybersecurity product.
In conclusion, rather than trying to seek relief through an insurance policy in the event of a breach, prevent the breach with the assistance of a provider that stands behind its promise!